Note: A modified version of this article was first published in DZone.
Welcome back! If you missed Part 2, check it out here.
Securing Data at Rest
Data at rest includes inactive data that is stored physically in any digital form (e.g. databases, data warehouses, spreadsheets, archives, tapes, off-site backups, mobile devices, etc.). Multiple AWS services provide built-in integration with AWS KMS to allow easy encryption of your persistent storage. These include Server Side Encryption for Amazon S3 and Amazon Glacier, multiple tiers of encryption for Amazon Redshift, and Transparent Data Encryption for Oracle and SQL Server databases via Amazon RDS. Moreover, you can now encrypt data stored on an EBS volume at rest and in motion by setting a single option. When you create an encrypted EBS volume and attach it to a supported instance type, data on the volume, disk I/O, and snapshots created from the volume are all encrypted. The most typical use case for data-at-rest encryption is encryption of S3 buckets. You have two options for this:
- Use Server-Side Encryption – You request Amazon S3 to encrypt your object before saving it on disks in its data centers and decrypt it when you download the objects.
- Use Client-Side Encryption – You can encrypt data client-side and upload the encrypted data to Amazon S3. In this case, you manage the encryption process, the encryption keys, and related tools.
You also have the option of implementing your own encryption-at-rest approach. For example, you can encrypt content locally and store encrypted content. Amazon S3 provides you the facility to upload an already encrypted object. It also provides the ability for you to upload an object along with an encryption key that’s used in-memory to encrypt an object. To retrieve the object, you must supply the same key.
The key AWS service that protects data at rest is AWS KMS, which provides an easy-to-use, secure, redundant, key management service. The following services are also components of the AWS strategy for protecting Data-at-Rest:
- Amazon S3 provides an object storage service that integrates with AWS KMS and allows you to supply your own keys. You can securely upload or download your data to Amazon S3 via the SSL-encrypted endpoints using the HTTPS protocol. Amazon S3 can automatically encrypt your data at rest and gives you several choices for key management. You can configure your S3 buckets to automatically encrypt objects before storing them in S3 if the incoming storage requests do not have the encryption information.
- Amazon EBS provides block storage integrated with AWS KMS. You can perform block-level encryption with your own operating system tools or third-party solutions. You can now encrypt data stored on an EBS volume by setting a single option. When you create an encrypted EBS volume and attach it to a supported instance type, data on the volume, disk I/O, and snapshots created from the volume are all encrypted. The encryption occurs on the servers that host the EC2 instances, providing encryption of data as it moves between EC2 instances and EBS storage.
- Amazon Glacier handles key management and key protection for you. Amazon Glacier uses one of the strongest block ciphers available, 256-bit Advanced Encryption Standard. In addition, if you want to (or are mandated to) manage your own keys, you can encrypt data prior to uploading it. Glacier has recently added Vault Lock. This new feature allows you to lock your vault with a variety of compliance controls that are designed to support such long-term records retention. You can now create a Vault Lock policy on a vault, and after it is locked, the policy cannot be overwritten or deleted.
Securing Data in Transit
Data in transit is any data that gets transmitted from one system to another. This includes communication between servers within your environment as well as communication between other services and your end users. By providing the appropriate level of protection for your data in transit, you protect the confidentiality of your application’s content. When protecting your data in transit, selecting protocols that implement the latest version of Transport Layer Security (TLS) is a common best practice.
AWS services provide many HTTPS endpoints for communication, thus providing encryption in transit when communicating with the AWS APIs. You have full control over your computing resources to implement encryption in transit across your services. Additionally, the AWS Certificate Manager (ACM) service provides you the ability to manage and deploy certificates for your domains.
Additionally, you can leverage VPN connectivity into your VPC or across your VPCs to facilitate encryption of traffic. When planning for an encryption-in-transit approach, consider your use cases and the balance between encryption and ease of use. Consider the use of VPN connectivity from your data center to AWS and look into HTTPS for secure application-to-application communication.
The key AWS service that protects data in transit is Amazon Certificate Manager (ACM), which helps you generate certificates used for establishing encrypted transport between systems.
AWS Certificate Manager (ACM) is a service that lets you easily provision, manage, and deploy public and private Secure Sockets Layer/Transport Layer Security (SSL/TLS) certificates for use with AWS services and your internal connected resources. SSL/TLS certificates are used to secure network communications and establish the identity of websites over the Internet as well as resources on private networks.
The following services and features also play a role in encrypting Data in Transit:
- ELB Load Balancers help deploy and manage load balancers using secure endpoints. One of the most important capabilities of the load balancer is its ability to perform SSL offload. In order to do SSL offload, the load balancer needs a certificate attached to one or more secured listeners. Elastic Load Balancing has recently been integrated with ACM to provision, manage, and deploy Secure Sockets Layer/Transport Layer Security (SSL/TLS) certificates. This allows seamless provisioning of ELBs with the required certificates.
- Amazon CloudFront supports encrypted endpoints for your content distributions. For web distributions, you can configure CloudFront to require that viewers use HTTPS to request your objects, so connections are encrypted when CloudFront communicates with viewers. You also can configure CloudFront to use HTTPS to get objects from your origin, so connections are encrypted when CloudFront communicates with your origin.
- AWS Shield is a managed Distributed Denial of Service (DDoS) protection service that safeguards applications running on AWS. AWS Shield provides always-on detection and automatic inline mitigations that minimize application downtime and latency, so there is no need to engage AWS Support to benefit from DDoS protection
Data Backup/Replication/Recovery
“If you store 10,000 objects with us, on average we may lose one of them every 10 million years or so. This storage is designed in such a way that we can sustain the concurrent loss of data in two separate storage facilities.” – Amazon
AWS provides you with multiple features and capabilities around data backup and replication. Amazon S3 is designed for 11 nines of durability for objects stored in the service, and it allows you to create copies of the content that can be replicated to other locations and AWS accounts for additional protection.
Amazon RDS performs snapshots or backups of your DB instances and allows you to replicate those instances to other locations. Snapshots can be taken of EBS volumes and copied across Regions. Additionally, you can automate tasks and scheduled jobs to perform backups of resources. Consider using a Lambda function to issue backups at an interval using CloudWatch Events.
Amazon Glacier is a secure, durable, and extremely low-cost cloud storage service for data archiving and long-term backup. Use this service for cost-effective storage of backup copies. These copies can be retrieved when needed for recovery, whether it’s for testing, compliance issues, or disaster scenarios.
The key AWS service that supports data backup, replication and recovery is Amazon S3. The following services and features are also important for backup and replication of data:
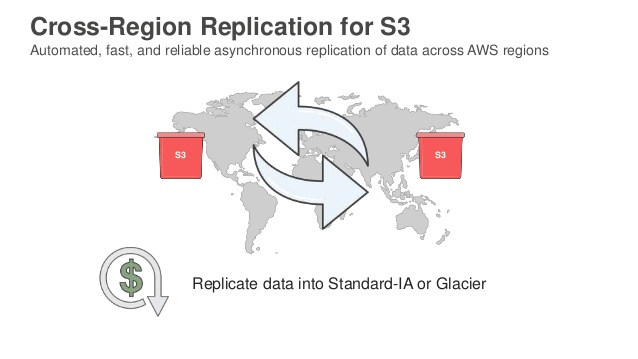
Amazon S3 Cross-Region Replication (CRR) is an Amazon S3 bucket-level feature that enables automatic, asynchronous copying of objects across buckets in different AWS Regions. Once enabled, every object uploaded to a particular S3 bucket is automatically replicated to a designated destination bucket located in a different AWS region. You can enable and start using this feature by simply enabling versioning. With versioning enabled, the rest is easy. You simply choose the destination region and bucket (and optionally restrict replication to a subset of the objects in the bucket using a prefix), set up an IAM role, and you are done.
Amazon S3 Lifecycle Policies and Versioning allow you to implement a backup strategy and meet retention requirements. You can use lifecycle policies to define actions you want Amazon S3 to take during an object’s lifetime (for example, transition objects to another storage class, archive them, or delete them after a specified period of time). You can define a lifecycle policy for all objects or a subset of objects in the bucket by using a shared prefix (that is, objects that have names that begin with a common string).
Amazon EBS Snapshots let you backup your volumes attached to EC2 instances. You can back up the data on your Amazon EBS volumes to Amazon S3 by taking point-in-time snapshots. Snapshots are incremental backups, which means that only the blocks on the device that have changed after your most recent snapshot are saved. This minimizes the time required to create the snapshot and saves on storage costs by not duplicating data.
This concludes the section on AWS native data protection services. When implementing encryption-at-rest and encryption-in-transit protection, consider the data classification model for your organization to ensure that the degree of data protection reflects your internal requirements. Additionally, you should consider any compliance or regulatory requirements. The key point here is that AWS provides mechanisms that allow you to apply encryption ubiquitously.
Incident Response
At first glance, incident response within AWS may appear more challenging than incident response in an on-premise environment. Not only are servers not physically available, but techniques associated with virtual machines such as taking a full disk and memory snapshot are not available. However, by leveraging the APIs provided by AWS, organizations can prepare themselves to automatically collect evidence and mitigate compromises of AWS instances. Before implementing such a solution, the organization should understand what preparations need to be made, mitigations need to be performed, and what evidence needs to be collected.
Before an incident ever occurs, an organization should ensure it has adequately prepared to deal with an incident. Determine the access your first responders need ahead of time, and then regularly verify the access is functional – or easily triggered – when needed. The two crucial response areas an organization should address include strengthening existing or available defenses to reduce the attack surface and increasing the organization’s ability to detect, remediate, and prevent future attacks. As we have already mentioned, AWS has many native security and monitoring services to assist in meeting these objectives, including CloudWatch, CloudTrail, Config, and IAM.
By using resource tags to properly describe your AWS resources, incident responders can quickly determine the potential impact of an incident. For example, tagging instances and other assets with an owner or work queue allows the team to engage relevant people more quickly. Moreover, by tagging systems with a data classification or a criticality attribute, the impact of an incident can be estimated more accurately.
For capturing the disk image or “as-is” configuration of an operating system, you can use EBS snapshots and the Amazon EC2 APIs to capture the data and state of systems under investigation. Storing snapshots and related incident artifacts in Amazon S3 or Amazon Glacier ensures that the data will be available and retained as appropriate.
During an incident, before the root cause has been identified and the incident has been contained, it can be difficult to conduct investigations in an untrusted environment. Unique to AWS, security practitioners can use CloudFormation to quickly create a new, trusted environment in which to conduct a deeper investigation.
The CloudFormation template can pre-configure instances in an isolated environment that contains all the necessary tools forensic teams need to determine the cause of the incident. This cuts down on the time it takes to gather necessary tools, isolates systems under examination, and ensures that the team is operating in a clean room.
Conclusion
Security is hard. We all know that. When an incident occurs it should be treated as an opportunity to improve the security of your infrastructure. AWS provides a spectrum of mechanisms for protecting data. Strong authentication and authorization controls, automated responses to security events, simple, cost-effective monitoring of systems and API calls, protection of infrastructure at multiple levels, and ubiquitous protection of data with encryption provide a level of defense-in-depth security controls that most organizations only aspire to.

